XLoader, which comes with its new version, is riskier as it requires almost no action compared to the previous one.
We have previously seen that malicious software that accesses user data causes large-scale effects both in our country and around the world. Aforementioned malware, caused great concern because it could even enter the bank account of the user without him/her noticing. Now, these software XLoadercomes to the fore with its new version.
The software, which was seen in places such as the UK, USA, Germany, France, Japan and South Korea with its previous version, can be installed on your phone surprisingly easily and can start working immediately. Of course, first of all, in the message you receive on your phone via URL You need to install the software.
It acts like Google Chrome.
Starts working immediately after installation XLoader“Ch.romtoIt asks for permissions such as being able to run in the background and read SMS using the name “. In one of them, it asks you to switch your default SMS app to Chrome. When it obtains all permissions, it can transfer photos, messages, contacts, hardware information and other data to its own server – the attacker.
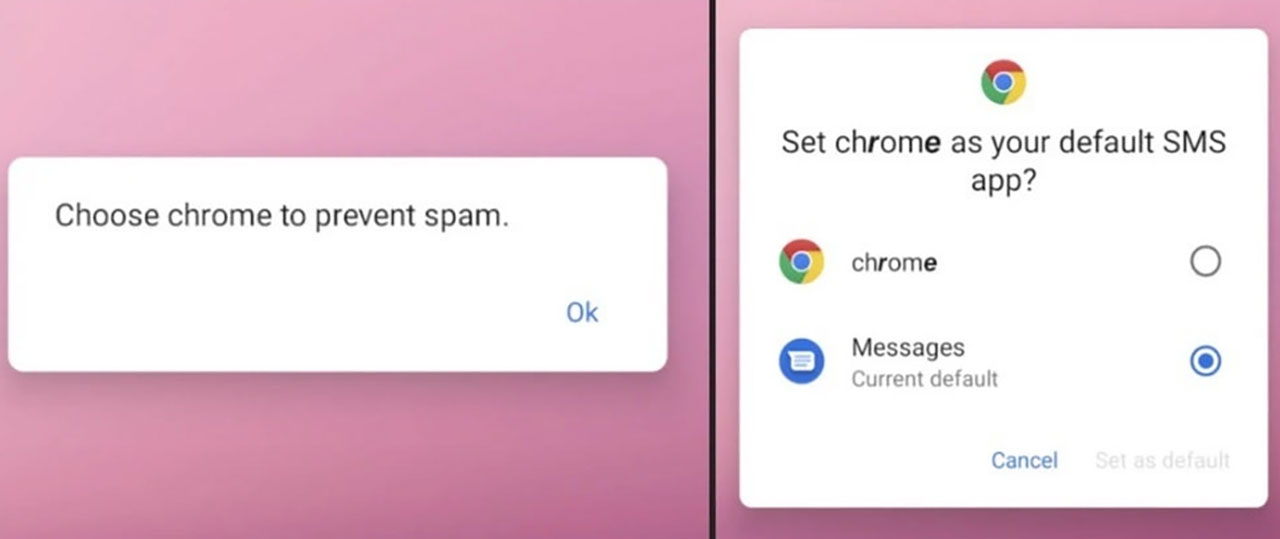
To protect you from this, Android devices are already Google Play Protect It comes with. But we should not rely entirely on this either. The most reliable method of protection is to avoid messages containing shortened URLs in the first place. not to open. Apart from that, it is also useful to be aware of which sites you use when installing applications from outside the Google Play Store.
McAfee stated that he forwarded this situation to Google and the situation was being worked on. He added that the software in question is more dangerous than the previous one, as it only needs to be installed for it to take action.
RELATED NEWS
How Are Phones More Resistant While Computers Catch Viruses Suddenly?
Source :
https://www.bleepingcomputer.com/news/security/android-xloader-malware-can-now-auto-execute-after-installation/
