Announcing it by ‘sharing a ticket photo’ on social media while going abroad or on vacation, although nice, carries great risks.
Many people who travel abroad or domestically on social media can innocently share photos of their tickets. Although this may seem like a harmless act, if careless big risks brings with it.
The plane tickets you share online can only be seen as a piece of paper that allows you to board the plane. However, this is not the case, these papers also contain your personal information, which allows the airline to easily access your information. So, how can this information be used against you?
Information on flight tickets:
Your flight ticket includes a barcode containing your name, surname and all your other information, along with the flight number of the plane you will be boarding, information such as your current location, your destination, where you live on the plane.
Even if this barcode, which contains your information and provides ticket verification, is not visible, the information on the ticket can be sufficient to learn most of the information about you. Just for the photo display of your surname and ticket number it’s enough.
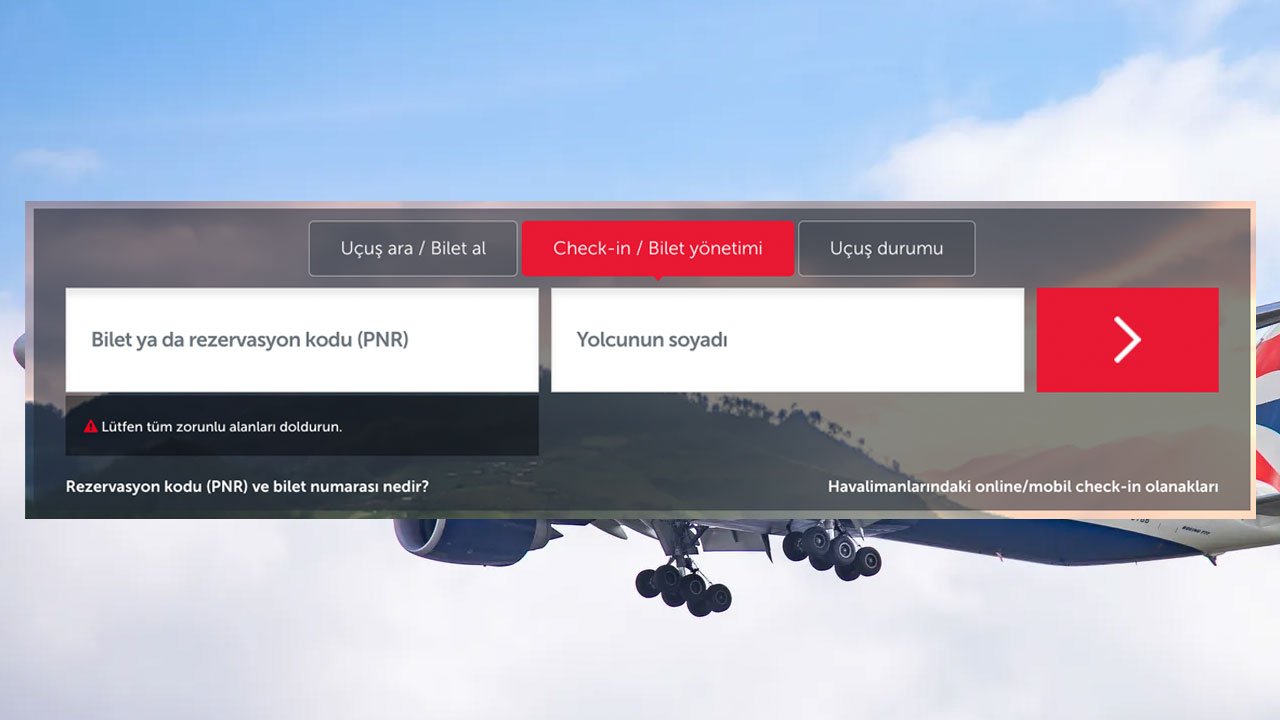
This information by entering the online check-in pages information such as a passenger’s e-mail address and phone number can be accessed. Unfortunately, many airlines do not host any verification method for accessing these pages.
How can the e-mail address and phone number that someone else learned through this method harm you?
- Your data can be included in a large data library without your knowledge. These data are available for sale later.
- People who learn or buy your data can send decoy messages to your phone number or e-mail address, and perform phishing attacks.
- If you accidentally fall into one of these attacks, all the information on your devices, your passwords, bank and credit card information can be compromised.
Many phishing attacks today are actually made with very convincing messages on e-mail and phone numbers in cumulative data libraries. So don’t say “I won’t fall”, take your precautions.
RELATED NEWS
