The Internet can also turn into a tool for malicious people, and these people can hack other users into their networks and capture their personal data using different methods. One of the most common social engineering methods they use for this is known as “Phishing”. So, what exactly is Phishing, how we can be protected, we have explained for you.
While surfing the Internet, we can sometimes come across files and applications that contain malicious software without realizing it. Antivirus programs compatible with both modern browsers and operating systems allow these software to be downloaded to the computer. substantially gets in the way. Unfortunately, the dangers of the Internet are not only not limited to software. Because malicious people know this, they attract users to their networks by establishing social relationships.
Malicious people who manipulate people using social engineering methods have also become extremely dangerous. Phishing method is one of the methods used by these people.
What is Phishing?
Phishing is a cybercrime committed by attacks against a target or targets via email, phone, text message or social media. The people who carry out these attacks send messages to their targets as if they are sending a message from an official institution. credit card, bank or other personal information they try to take over. As a result of the information that is believed and sent to these people, people become victims. Phishing is one of the greatest examples of social engineering.
What are the common features of phishing attacks?
- They make offers that are too good to be true,
- Expressing urgency and being persistent,
- Hosting fake links with subtle changes,
- Plugins,
They make offers that are too good to be true:

What is called social engineering requires humans to gain access to computer systems. manipulate, influence, or deceive is art. If you are under a phishing attack, one of the first and most obvious steps to understanding it is to tell you. look at the content of the sent message will be. Emails or messages sent for the purpose of a phishing attack offer extremely good offers in it.
If there are good offers that you did not even think of in the message sent to you, or if expressions that will attract your attention are used, you should not come to the fishing line immediately. For example, in a randomly sent e-mail you have won an expensive smartphone or if it says you’ve won a different, expensive prize, it’s probably a It’s a phishing attack. If a message seems too good to be true, it’s definitely suspicious.
Expressing urgency and being persistent:

One of the most common tactics of cybercriminals is your they want you to act fast. They try to do this by saying that this award, campaign or discount given to you is valid for a very short time. The reason for this is by entering the minds of users. excitement and urgency Trying to bring out the feeling. In this way, people who view the e-mail content can carelessly click on the link and transfer the information to the other party.
So much so that in some messages, the sender only tells you. a few minutes may indicate that you are facing an offer. In addition, in phishing attacks, messages such as your account will be closed if you do not change the information of any of your social media accounts. If you are receiving such messages, all you have to do is ignore or even delete this message.
Hosting fake links with subtle changes:

The worst move you can make as an internet user is to blindly click on the link that appears. It’s like jumping blindfolded into a deep pool where you don’t know whether it’s full or empty. There are also such links in e-mails and messages sent in phishing attacks. Although these links seem quite natural at first glance, it is actually necessary to be very careful.
The people who make these attacks may try to steal your information by including links that are not real in the e-mails they send to you. To give an example: A real website, www.webtekno.com, may appear as www.webtecho.com in the e-mail sent for the purpose of a Phishing attack. If you don’t pay attention, small replaced by letter games you can access these fake web pages and You can lose your data.
Plugins:
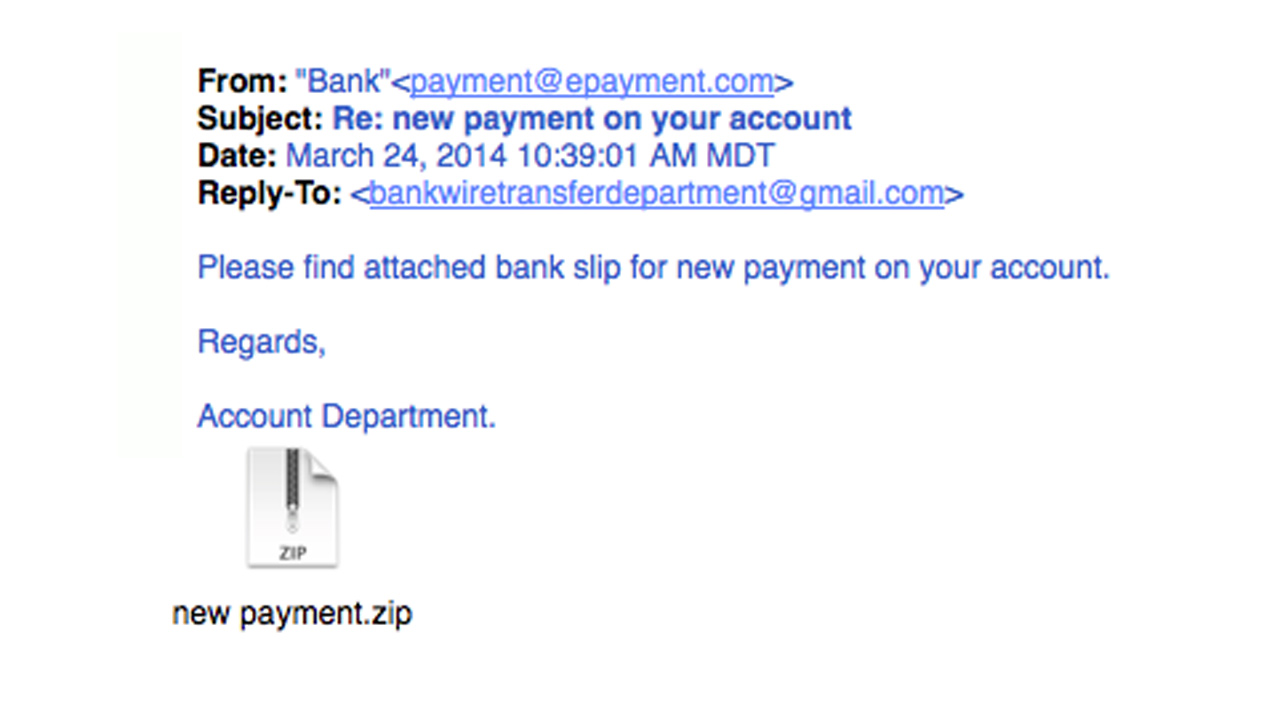
Emails sent for the purpose of phishing attacks often have attachments to make them credible. These attachments should not be opened if the e-mail did not come from an expected place. In these plugins may contain malware and from the moment it is downloaded and opened, it begins to spread viruses to the computer. Therefore, it is extremely important to be cautious about the plugin.
What are the ways to protect from phishing attacks?
- Use spam filters,
- Be careful when clicking links.
- Check the sender,
Use spam filters:

The first way to block e-mails sent for the purpose of a phishing attack is to keep your e-mail and other messaging applications safe. Activating spam filters will be. These spam filters are generally found in all messaging applications and e-mail services and have an algorithm that detects spam by checking the content of the e-mail or message and the person who sent them.
Spam filters are not always 100% accurate, and some real emails and messages may end up in the spam box, but most emails and messages that are sent for the purpose of a phishing attack are generally will be caught in spam filters. So the first thing you should do is to activate the spam filters if they are not turned on.
Be careful when clicking links:

As we mentioned when explaining common Phishing methods, although the links in the messages sent seem to be correct, misleading it can happen. Therefore, you should check the link thoroughly before clicking on any link. After checking the details such as if there is any letter change, if the address is correct, if you still have doubts, reach the official page of the link sent to you via Google and then follow the necessary steps and enter the part in the link sent to you.
In addition, it determines whether websites are safe or not. SSL Pay attention to the certificate. All websites with this certificate “https” It starts with and is reliable. If you see “http” instead of https, you should not log into that site. Most browsers automatically block access to such sites, but you, as a user, need to be careful.
Check the sender:
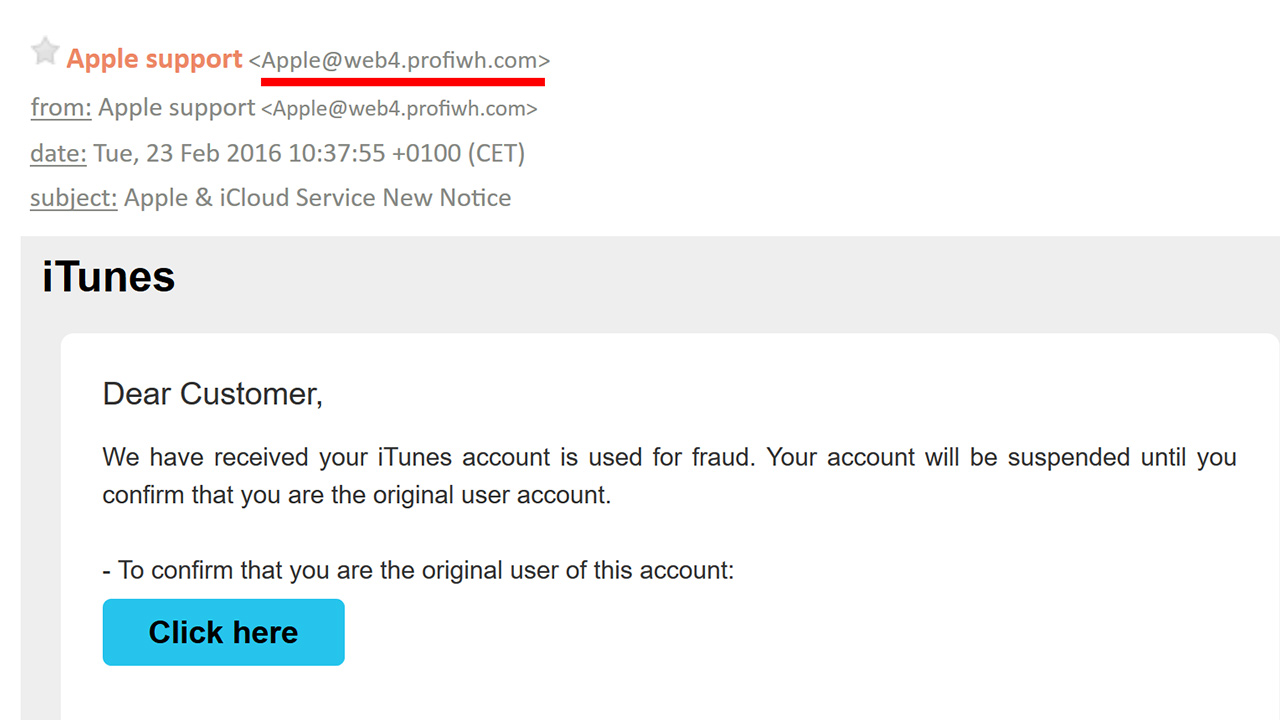
Emails and messages sent in phishing attacks are generally by someone at the company you work for or an organization you are in. are sent from private email addresses to appear as sent. Before you believe or trust such e-mail addresses, go through a few steps and check if they are reliable.
First, look at the email address of the person who sent the email and see if that person usually emails you. Check. If he doesn’t usually email you and you suddenly get a strange, irrelevant email, don’t open the message. If it’s from someone you know but you’re not aware of, talk to that person on a different platform and ask if he or she sent the email.
What is Phishing? We have come to the end of our guide content, where we answer the questions of what are the ways to be protected from phishing attacks. If you want more of our guides like this one comments You can state your opinion in the section. Follow us so you don’t miss out on more content like this.