In these times when technology is developing considerably, fraudsters continue to improve themselves. You will be shocked to learn how scammers deceive people with unimaginable methods.
Everything you can think of, from accessing your computer, tablet or phone camera to learning your card passwords. In the century of technology It is possible as of today. Using a new method every day, people, sometimes even even the states As you can imagine, these situations that lead to dangerous events are a very big threat.
We also provide you with information about what might happen to you if you encounter this threat. worst case scenarios We ranked and cyber security expert Yasir GokceWe talked to and explained how they use these methods:
The first question we asked him was “How come when we click on the link sent by fraudsters, they can access all our files?” was the question. Here are Yasir Gökçe’s answers:
The most commonly used method in this type of attack is a type of attack we call “drive-by download”. The victim of this attack opening a particular file or clicking on a site is sufficient. Afterwards, the malware or code is automatically installed on the computer and your computer’s protection and operating system are damaged. according to the current level activates itself.
downloaded to your computer and Self-destructing malware, although sometimes harmless “adware” well as unwanted advertising While it can show its effect, it can also present more harmful cyber threats to the target. This effect may be caused by malware or by type of code Varies: Virus, trojan horse, logic bomb, spyware, worm, cryptojacking etc. Depending on the situation, different harmful consequences may occur.
These malware sometimes you do not allow It manipulates the permissions of social media applications to share your information and may change them without your knowledge. Sometimes the internet The area where your traffic information is stored or by manipulating the table, it directs your internet traffic to its own network and captures your sensitive information.
But that’s not the worst part: access with advanced privileges It installs malware as needed. For example; By installing cryptominer, you can take your entire system hostage. cryptojacking Also known as.
Another bad scenario is that they can access the cameras of our vehicles such as phones, tablets or computers. So how do they do this?
As with every cyber attack “camfecting” In this type of attack, the cybercriminal gains access to our system and begins to abuse this access. This attack is particularly laptop, television, telephone or CCTV It is a threat to information systems that contain cameras, such as, and it proceeds by gaining access to the relevant system via remote access and using the authorization escalation method known as “privilege escalation”.
This cyber attack usually “Remote Access Trojan” malware called is used. The cybercriminal, who infected the system and managed to increase the privileges to the desired level, used software or programs that used cameras for camfecting. browser add-ons downloads and activates them.
These continue to work in the background without us realizing it. Even the camera LED light not on It was activated in 2013 macbook It was revealed in a PenTest study conducted on .
How can we protect ourselves from this situation?

Even though you are not using a camera, if your camera light is on, you can use the camera immediately. Whether applications are open should be checked. You can do this by entering your computer settings and typing “camera settings”. Even though the browser is not open If the camera is active, The problem is in browser add-ons.
Relating to by removing or deleting the plugin You may find a solution, even if it is temporary. Apart from these, you can also check whether there are any unintentional camera recordings by going to the file where your computer’s camera recordings are kept. As a general solution, many people use their cameras nowadays. with the help of a band can turn it off.

Most importantly, your computer’s operating system and software kept up to date. An up-to-date antivirus program plays a big role in preventing and fixing the problem. Users with high technical knowledge protocols and services They can deactivate the access through the firewall, if necessary.
RELATED NEWS
Security First: What is Firewall and What Does It Do?
With today’s technology, it is possible for them to learn our credit/debit card passwords from keyboard movements. How can they do this?

One of these methods is keylogging to the computer, that is, recording the keyboard keys. recording the editions is to add a part that resembles a hardware USB. Alternatively, an actor who has already accessed the system keylogger software You can download and run it and record the keyboard key presses this way.
Moreover, Keyboards with Wi-Fi The most serious part is vulnerable to “KeySniffer” attack. In these keyboards, signals or packets are transmitted over insecure radio protocols and are not encrypted.
The attacker can intercept and analyze this unencrypted signal transmission by placing a KeySniffer near the keyboard. This is why keyboards connected via Wi-Fi should be avoided and Bluetooth or wired keyboards should be preferred.
Finally; speed, hardness, duration and intensity of pressing the keyboard understands which button is pressed artificial intelligence applications are being developed. Additionally, the sounds made by the keyboard key understanding the difference in nuance There are artificial intelligence studies. Cybersecurity experts predict that artificial intelligence will be used by cybercriminals for this purpose as well.
Some links, especially those sent via e-mail, may be exactly the same as the original domain addresses. How can we distinguish this?
Using a method called spoofing, the e-mail header is manipulate It is possible to. For this, you need to use an e-mail server such as Outlook, Gmail and Simple Mail Transfer Protocol, which is not considered secure. (SMTP) protocol is sufficient.
In this way, the content in the e-mail header “sender, reply or return” Information such as this can be created separately from the e-mail body. SMTP does this There is no mechanism to verify so it cannot detect whether the email is genuine or not.
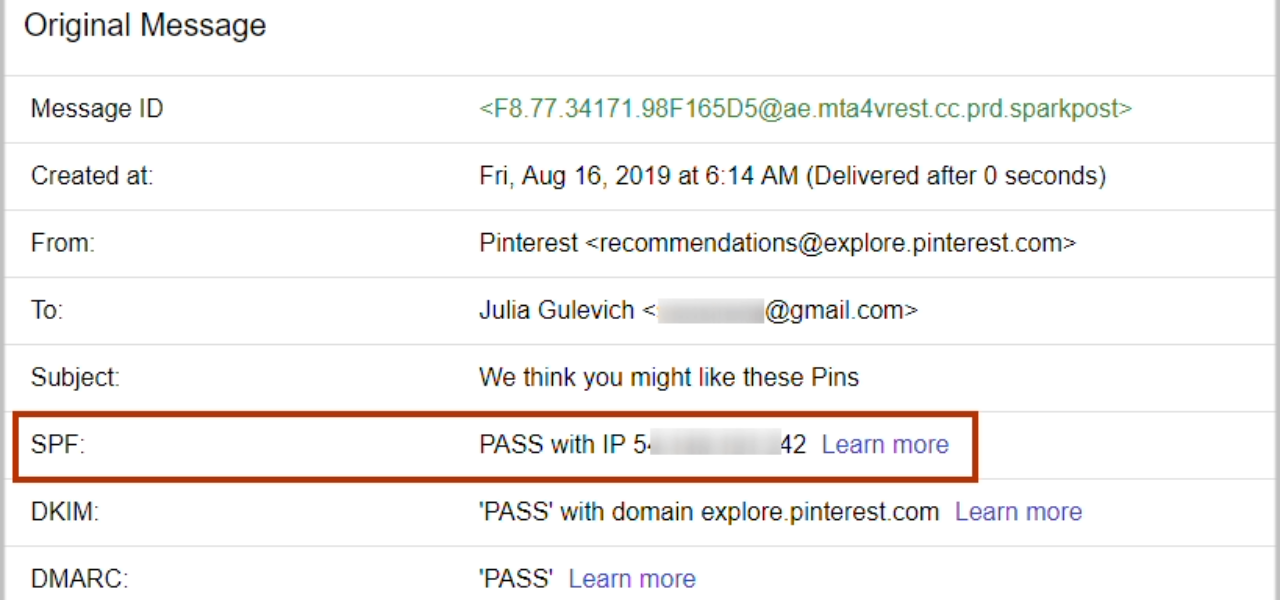
To detect e-mail fraud, message content and quality should be examined and serious spelling and contextual errors It should be checked if there is any. Additionally, there must be harmony between the sender and recipient information in the e-mail header and the e-mail address.
Also, RECEIVED-SPF against the knowledge “Pass” phrase should take place. The phrases “Fail” or “Softfail” included here sign of fraud It does. Externally, secure email protocols should be used. (For example, SPF, DKIM, DMARC etc.)
And finally, what kind of bad scenarios await us apart from the above? Is there anything worse than these?

Apart from cyber attacks that cause physical effects in the physical world and can cause injury and death, states too has had its share of these cyber crimes.
For example; Russia gained access to the control systems of a Ukrainian power plant and people without electricity to let go or the USA’s control of a significant part of the Natanz uranium facilities in Iran. through hacking Harm (Stuxnet incident) can be given as an example.
After this attack, a device that can be controlled by digital means dam gates can be opened; on the train tracks level crossings can be manipulated or tampered with personal medical data in the hospital.
I’ve talked to him before about “What should you do if you click on a link and get hacked?” We shared a themed content:
RELATED NEWS
What Should You Do When You Get Hacked and Have Your Information Stolen Just Because You Clicked on a Link? (Recommendations from Experts)
What we mean is that you click on every link, site or e-mail you see on the internet. not to click There are benefits. cyber security expert Yasir GokceWe would like to thank for sharing this information with us and wish you to surf the internet in a safe environment!
RELATED NEWS
The “Slave Trade” of Cyber Fraudsters Has Been Exposed (Your Blood Will Cold While Reading)
RELATED NEWS
We Explained the Fraud Methods That Have Been Frequently Seen on Social Media Lately: You Should Be Careful!
RELATED NEWS
The Real Face of Foreign Numbers That Recently Send “Hello” to Everyone on WhatsApp
RELATED NEWS
We Talked to Fake Diploma Scammers: When You See Their Answers, “Are Our Lives That Cheap?” You will say!
RELATED NEWS
New Claims About the Website Sharing All of Turkey’s Identity Information for Free: It Has Data of 101 Million People, Not 85!
RELATED NEWS
